It is easy for users of cloud accounts such as G Suite (previously Google Apps), Office365, Dropbox or any of the myriad of other cloud vendors to assume that, because their data is backed up in the cloud, they are safe from a ransomware attack - but that is not the case.
To find out how to protect your organisation, see below.
- Had not installed the latest security patches from Microsoft
- Did not have up-to-date anti-virus software installed
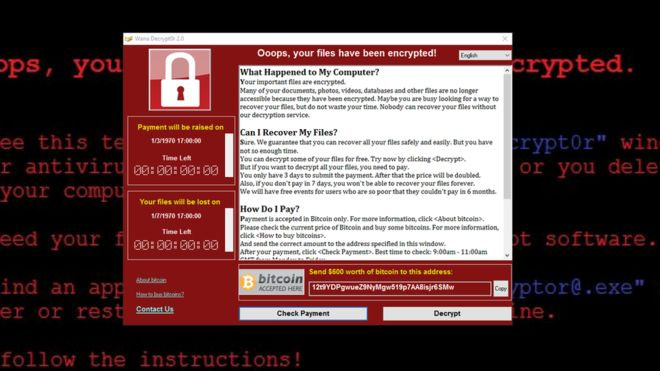
If your computer is infected, all of the files on the machine are locked and your access to your data is prevented until you either restore from the latest back up or pay the ransom.
Collaboration platform vendors like Microsoft and Google provide strong capabilities to help protect their customers’ data, but customers must also protect themselves.
SaaS providers focus on preventing cybersecurity attacks, with data security scanning, malware detection and prevention, but these controls cannot fully prevent cybersecurity attacks that lead to data loss. Microsoft and Google will also protect your data against hardware or software failure, natural disasters, or power outages, but SaaS applications can’t fully protect customers from data loss caused by Ransomware, sync errors from integrations, or human error.
Why not? Well, to the SaaS provider, when data gets encrypted, changed or deleted by Ransomware, sync errors, or other destructive activity, it looks just like data that was changed or deleted by you, the customer, for legitimate reasons. There is no way for the SaaS provider to know that something untoward has happened. This is why you must protect yourself against the data disasters that continue to occur every day.
The alarming growth in ransomware poses a particular threat for those organisations using SaaS collaboration platforms like G Suite and Office 365.
Because the responsibility for data protection falls to the customer, and because these platforms speed collaboration by making files and folders easy to share, automatically syncing changes – a ransomware attack can lock shared files at compute speed. One Spanning Backup customer reported that a ransomware attack locked nearly 950 files in a few minutes.
“At about 7:50 AM, one of our users saw a message open on their screen, saying their files had been encrypted and locked, and they needed to pay ransom to access their files. By 8:00 AM – ten minutes later! – a number of other users called our IT support desk saying file names had been changed.
“The malware went through complete hard drives in seconds and encrypted EVERYTHING. And as shared documents in synced folders became encrypted, other docs in those folders were encrypted. In just a few minutes, the ransomware attack on one synced folder alone encrypted almost 950 files!”
How can you protect your organisation?
Some best practices include:
Pre-attack
- Train end users to be more phishing-resistant and hack-savvy
- Identify high-value spear-phishing targets, and review / restrict their folder and file sync to limit the impact if ransomware infects your organization
- Evaluate and acquire an enterprise grade cloud-to-cloud automated backup solution with robust restore capabilities; monitor backup status
- Periodically test the restore process to ensure restored files from backups are usable
- Isolate the infected assets quickly – if needed, unplug physical PCs, turn off all syncing for SaaS applications, and shut down network access
- Determine whether the infection is “scareware,” or a low-level hack causing a browser screen “law enforcement warning” without true file encryption – if so, use Windows Task Manager to close the browser, or force quit on Macs
- If not scareware, research whether there is a known decryptor app – however, it may not be possible to recover your files if the ransomware has robust encryption
- Run an antivirus program on the infected devices to remove the malware
The customer story noted above has a happier ending than most ransomware stories.
“Fortunately, we had Spanning deployed. The infection wasn’t robust – but it did make a mess that I estimate it would have taken the IT team a full two days to recover from. With Spanning, the time it took to recover was about 3 hours – about 100% faster than we could do without Spanning. We are very glad we had Spanning backing us up prior to this attack!”
If you’re not using Spanning Backup to protect your G Suite or Office 365 data, you should evaluate whether it would improve your RTO before ransomware infects your organisation.
SmartCloud is an authorised Spanning Backup Reseller. To get Spanning set up on your G Suite or Office365 domain, contact us.




 RSS Feed
RSS Feed









